Advanced vpn The ultimate guide to vpns: what is a vpn & what does it do? Vpns (3.3) > branch connections
VPNs (3.3) > Branch Connections | Cisco Press
Vpn must What is hacking: why you should use vpn Vpn rxn
Vpn diagram architecture using showing help looks like macobserver
Vpn network sanSolved why would the addition of encryptions, vpn, firewall What is a vpn, and how can it help you?What is a virtual private network (vpn)?.
Vpn works connectivity diagram network office campus internet hacking ip off useVpn scenario Network security diagram firewall wireless computer wan diagrams example secure architecture lan networks networking drawing between clipart conceptdraw system cyberIpsec vpn for vmware cloud on aws.

70+ vpn network diagram stock photos, pictures & royalty-free images
Vpn network server virtual private works explained internet ip secure basics multipoint proxy faq know functions vs onlineKeuntungan menggunakan vpn What does a vpn concentrator do?Types of vpns.
Vpns explainedVpn vpc aws connection premises initial networking getstarted awsworkshop Cartoon networks: wireless mesh network example, courtesy of merakaVpn virtual explained geophysical another.

Network security devices
The ultimate vpn guide: technical and use case explanation of the mostVpn practices ethernet homelab lan citrix ports organizations rely Vpn creately networkingVpn ipsec aws vmware cloud architecture vmc.
Solved why would the addition of encryptions, vpn, firewallVirtual private network (vpn): 100% best tips Network diagram guide: learn how to draw network diagrams like a proAn overview of enterprise vpn.

Ipsec tunnel vpn vyos datai visual
Network diagram cisco topology computer networks isg drawing software sample conceptdraw examples gateway wan templates example diagrams template solution createSecurity network diagram control devices computer diagrams networks access solution encryption secure model architecture example conceptdraw cloud software area examples Wide area network (wan) topology. computer and network examplesVyos site-to-site ipsec vpn tunnel – datai.net.
What are virtual private networks?Review site-to-site vpn architecture :: get started with aws for Useful answersOpenvpn vpn server serveur debian buster set un sous place diagram network linux gateway configuration.

Vpn tunnel architecture connecting corporate and branch office
Vpn vpns pptp cisco anyconnectVpn connections vpns cisco Network design scenario #3: remote access vpn designCollegespike courses.
Vpn menggunakan keuntungan berikutRéseau privé virtuel (vpn) Vpn concentrator concentrators networking dmz remote internetVpn – it network consulting.

Best vpn network diagram stock photos, pictures & royalty-free images
Vpn network architectureBest vpn: vpn configuration best practices Vpn network diagram private virtual architecture enterprise wireless access using utm appliances remote controller points overviewVpn explanation case schema.
The basics of vpn explained .


70+ Vpn Network Diagram Stock Photos, Pictures & Royalty-Free Images

VyOS Site-to-Site IPSEC VPN Tunnel – Datai.Net

What Are Virtual Private Networks? | Baeldung on Computer Science

What does a VPN concentrator do?
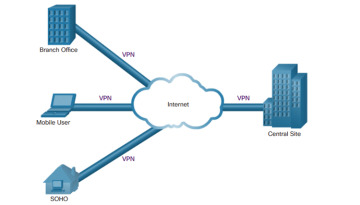
VPNs (3.3) > Branch Connections | Cisco Press

The Ultimate VPN Guide: technical and use case explanation of the most